Is Your Password Crackable?
 Web Applications like phpBB, WordPress, almost all online apps with authorization capability store user passwords by creating an encrypted hash of your password. The hash is unique to the password so hashing the password in the future will result in the same hash every time.
Web Applications like phpBB, WordPress, almost all online apps with authorization capability store user passwords by creating an encrypted hash of your password. The hash is unique to the password so hashing the password in the future will result in the same hash every time.
Usernames and Hashes
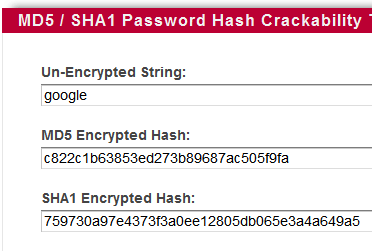
So if your password is google and your username is rocks, your app will store you as [user:md5 hash of google] When you enter your username and password to login later, the app compares the md5 hash of your submitted password to the stored hash.
rocks=c822c1b63853ed273b89687ac505f9fa
Cracking Hashes
A hash is encrypted, meaning you can't reverse-engineer it to find the plain-text. So to crack a hash you have to create a hash for each guess until the hashes match, which tells you the plain-text of the encrypted password.
Rainbow Tables
To speed up this process programmers have created pre-generated tables containing trillions of [plaintext=hash]. So you can quickly search a table for the encrypted hash, and if it finds a match it tells you the decrypted plaintext string.
Test Your Password
I've put up a new tool to check the strength of your password hash, which you can use to see if one of your md5 or sha1 password hashes have already been cracked (meaning they are in the rainbow table), so you can be proactive in your security posture.
If you have a user account on forum software like phpBB, or really any web application that stores hashes in a database of some kind, you should find your hash and test it. If it is cracked then you should change your password to include both numbers, symbols, and letters at least 8 characters long.
You can also enter in a plaintxt password and the tool will compute the md5 and sha1 hashes of that password and test those. Your plaintext password is never directly sent to a server, but the md5 and sha1 hashes are.
« Firefox Adsense WordPress PluginHackers Declare Total War against Scientology »

Comments