Watch Dogs 2
 This trailer speaks to the current state of the Internet of Things, and what we can expect over the next several years.
This trailer speaks to the current state of the Internet of Things, and what we can expect over the next several years.
 This trailer speaks to the current state of the Internet of Things, and what we can expect over the next several years.
This trailer speaks to the current state of the Internet of Things, and what we can expect over the next several years.
Secure WP Super Cache, Anti-exploits, Mitigation techniques. A bunch of current ways to stop wordpress exploits and spam. 
Unix file permissions are one of the more difficult subjects to grasp.. Well, ok maybe "grasp" isn't the word.. Master is the right word.. Unix file permissions is a hard topic to fully master, mainly I think because there aren't many instances when a computer user encounters them seriously, and bitwise is oldschool. This contains a listing of all possible permission masks and bits from a linux, php, and web hosting view.... cuz you guys AskApache Regs Rock!
Sometimes there is an urgent need for creating an exact duplicate or "mirror" of a web site on a separate server. This could be needed for creating Round Robin Setups, Load-Balancing, Failovers, or for just plain vanilla backups. In the past I have used a lot of different methods to copy data from one server to another, including creating an archive of the whole directory and then using scp to send the file over, creating an archive and then encrypting it and then sending that file over using ftp, curl, etc., and my persistence at learning new ways to do things has paid off because now I use rsync to keep an exact replica of the entire directory on an external server, without having to use all the CPU and resources of other mirroring methods.
A list of API Versions and the corresponding HTTPD Version, for use in determining the version of Apache currently running without having to rely on the often inaccurate SERVER_SOFTWARE Header.
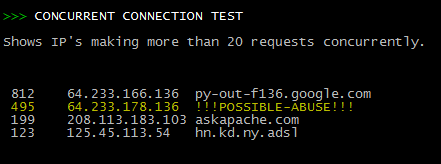 Scan Apache logs for IP address that are probably evil, then generates an .htaccess file to DENY them all.
Scan Apache logs for IP address that are probably evil, then generates an .htaccess file to DENY them all.
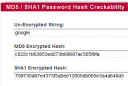 I've put up a new tool to check the strength of your password hash, that locates weak passwords by searching Rainbow Tables for md5 or sha1 hash match. Locate and fix this common security vulnerability before being exploited.
I've put up a new tool to check the strength of your password hash, that locates weak passwords by searching Rainbow Tables for md5 or sha1 hash match. Locate and fix this common security vulnerability before being exploited.
While testing the exploitability of your target and mapping out vulnerabilities it is important to gain access inside the targets defenses so that you can establish an internal foothold like a owned box or switch. This is so you can use a tool to discover the packet-filtering being used, and literally map out the firewall/IDS rules. Needless to say that really provides you with a lot more complete vulnerability assessment to help discover more weak spots in the system.
Tons of awesome tips and tricks using netcat. Port redirector, nessus wrapper, capture exploits being sent by vuln scanners, etc. This is very useful for doing stuff like redirecting traffic through your firewall out to other places like web servers and mail hubs, while posing no risk to the firewall machine itself.
 I've tried 100's of Anti-virus, Anti-Rootkit, and Anti-Spyware tools over the last 10 years, but it's always good to re-examine your system's security every couple of months.
I've tried 100's of Anti-virus, Anti-Rootkit, and Anti-Spyware tools over the last 10 years, but it's always good to re-examine your system's security every couple of months.
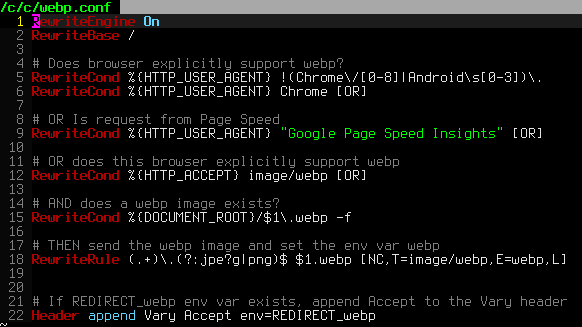 .htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.
.htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.
You've come to the right place if you are looking to acquire mad skills for using .htaccess files!